THE SOLUTION TO DATA VULNERABILITY, EXFILTRATION, AND EXPLOITATION
HOW DOES CYBRLOCK DELIVER WHAT NO ONE ELSE CAN?
WHAT DOES
CYBRLOCK PROTECT?
WHY IS CYBRLOCK CALLED 'THE SOLUTION' TO DATA COMPROMISE?
THE SOLUTION TO DATA VULNERABILITY, EXFILTRATION, AND EXPLOITATION
HOW DOES CYBRLOCK DELIVER WHAT NO ONE ELSE CAN?
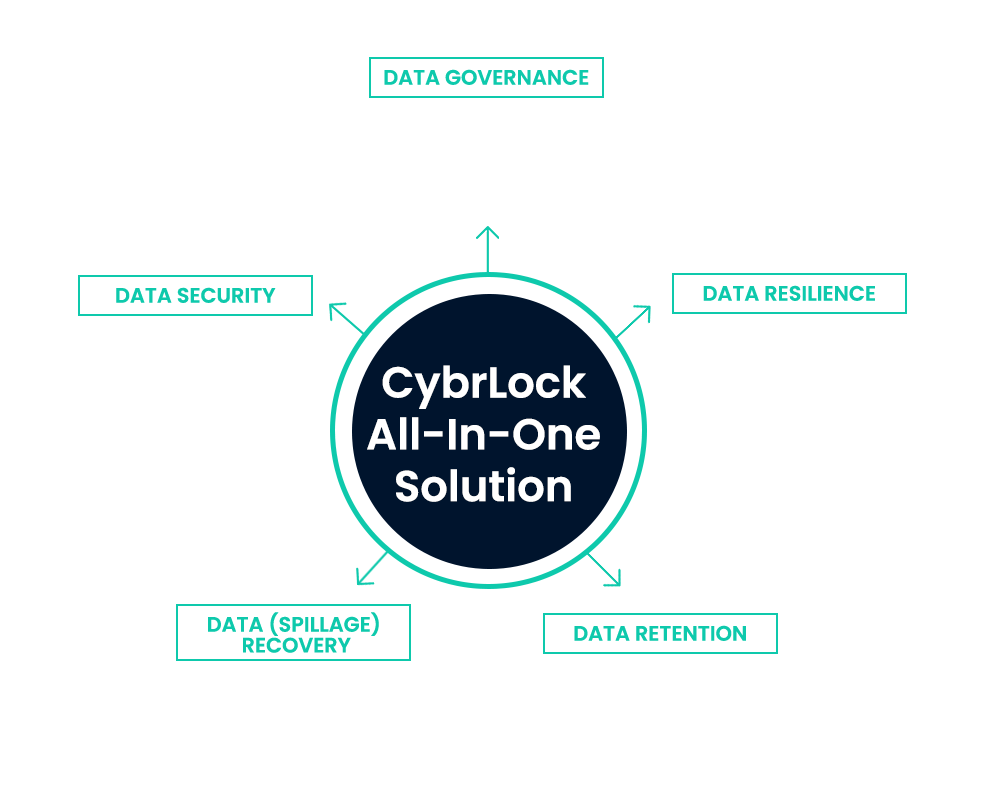
WHAT DOES
CYBRLOCK PROTECT?
WHY IS CYBRLOCK CALLED 'THE SOLUTION' TO DATA COMPROMISE?



[email-download download_id=”9207″ contact_form_id=”2842″”]