Tour all features
Whether you’re ready to speak with someone about pricing, want to dive deeper on a specific topic, or have a problem that you’re not sure we can address, we’ll connect you with someone who can help.
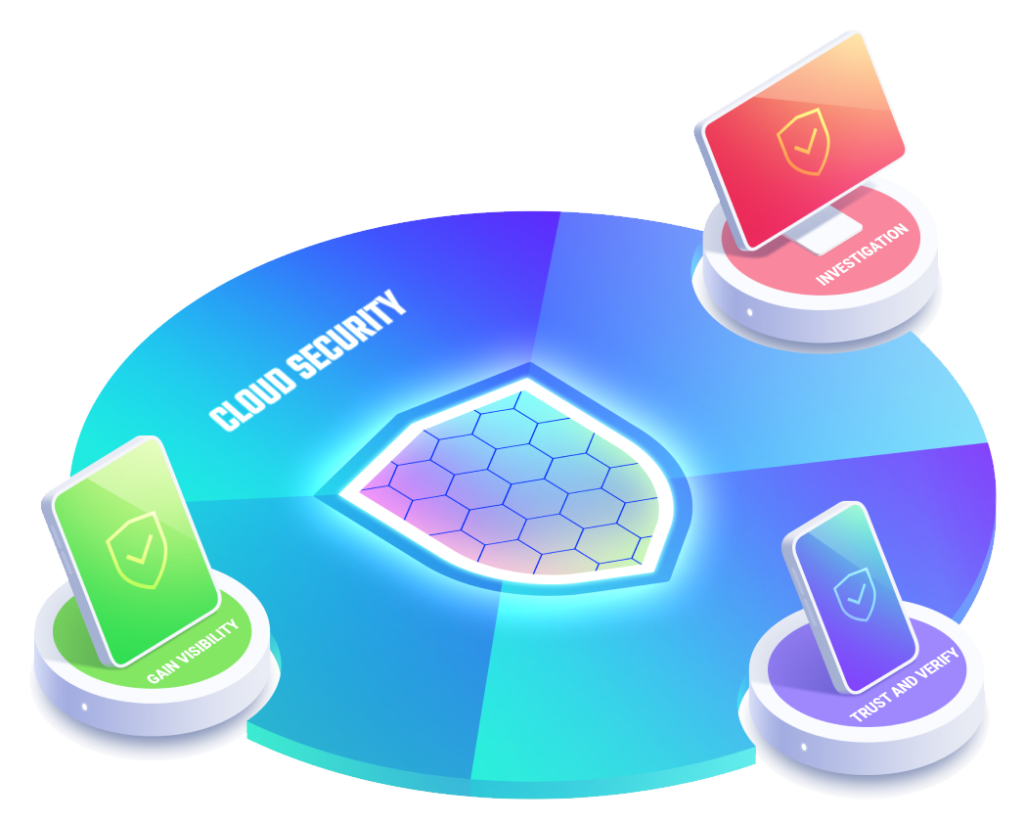

Ensure that you have a window into the workload, both in real-time and historically.
Use policy-based behavioral monitoring and investigate with cloud context

Trust is essential to move and build quickly. but verifying Business-critical activity is key to managing risk effectively.







[email-download download_id=”9207″ contact_form_id=”2842″”]