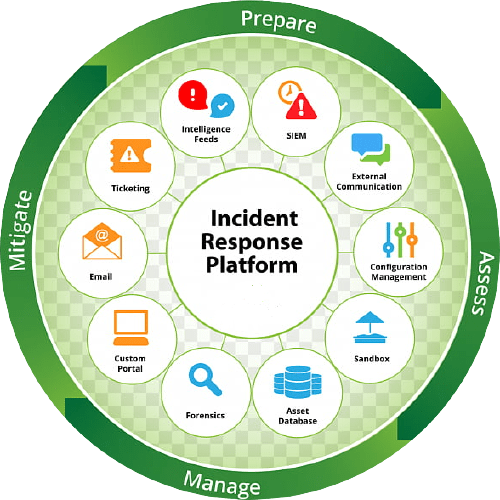
CybrHawk Incident Response & Management
CybrHawk helps you to identify threats in your network infrastructure and provide you with solution including improvement on the command line. Audit teams can save 3 to 4 hours per device using CybrHawk (as compared to manual testing). You may employee available best practices or use innovative industry compliance criteria such as STIG & CIS benchmarks.