Let HawkINT monitor, scan, and classify the cyber threats affecting your business—across the surface web, deep web, and dark web. Leverage over 12,000 bots and 380+ data sources to detect attacks, leaks, scams, fraud, and emerging cyber threats before they impact your organization.
In today’s dynamic cybersecurity landscape, it is essential for organizations to adopt established and proven frameworks to ensure effective compliance. With a multitude of frameworks available, selecting the most suitable one becomes a prudent choice. As regulations evolve and expand their scope, previously unaffected business sectors are now drawn into the compliance ambit. Consequently, the cybersecurity landscape undergoes continuous changes and evolution. By strategically choosing and implementing the right frameworks, businesses can adapt to these shifts, enhance their security posture, and stay resilient against emerging threats.

The Critical Infrastructure Cybersecurity Framework, also known as the Cybersecurity Framework, is a collaborative set of guidelines designed to assist organizations in effectively managing and mitigating cybersecurity risks.
The Data Security Standard of the Payment Card Industry (PCI DSS) is a compliance system providing mandatory standards for entities handling credit card data. Its objective is to protect the identities and information of the holders of the payment card (credit or debit card) and is made up of multiple requirements this corresponds to the extent to which credit or debit card information interacts with an organization. So banks, financial institutions, business enterprises and service providers tend to have to fulfill more conditions of compliance than other organizations.
The 2002 Sarbanes-Oxley (SOX) Act created a system for mandatory public company controls. It was passed in the aftermath of Enron, WorldCom, and Tyco accounting scandals that destroyed the confidence of investors.
The International Organization for Standardization (ISO) is a comprehensive and international set of standards that aim to improve and report on quality management and security across a range of industries. Within the larger ISO framework, there are different sub-frameworks, with conditions that apply to specific market sectors and disciplines.
The recently adopted General Data Protection Regulation (GDPR) is a compliance framework setting out strict conditions, guidelines and penalties for organizations and individuals collecting, storing and processing personal information from citizens and residents of the European Union (EU). The GDPR is one of the most important mechanisms that have ever been designed to protect citizens ‘ data privacy. It has a global obligation, as its terms extend to any company or entity in any part of the world dealing with EU customers or users ‘ personal data.
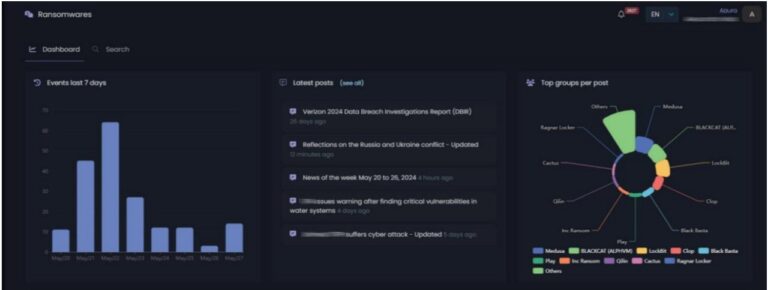
HawkINT is an OSINT and CTI platform designed to track, analyze, and respond to diverse threats. Our SaaS platform continuously monitors open sources, deep web forums, dark web markets, and high‑risk digital environments to bring full visibility of external risks.
Harden the environment and enforce least privilege—without slowing the business.

Thousands of specialized bots scan millions of posts, files, pages, and conversations across:
When HawkINT detects threats—like phishing pages, leaked credentials, fraud schemes, hacktivist planning, or illegal data marketplaces—the system creates “wires” with solid evidence, context, and recommendations.
Security teams can also configure custom alerts to detect threats related to VIPs, vulnerabilities, brand impersonation, or domain abuse.

In today’s dynamic cybersecurity landscape, it is essential for organizations to adopt established and proven frameworks to ensure effective compliance. With a multitude of frameworks available, selecting the most suitable one becomes a prudent choice. As regulations evolve and expand their scope, previously unaffected business sectors are now drawn into the compliance ambit.
Regulatory compliance regimes usually set out highly specific and often strict criteria to be met by organizations and under existing legislation.
In today’s dynamic cybersecurity landscape, it is essential for organizations to adopt established and proven frameworks to ensure effective compliance. With a multitude of frameworks available, selecting the most suitable one becomes a prudent choice. As regulations evolve and expand their scope, previously unaffected business sectors are now drawn into the compliance ambit.
Consequently, the cybersecurity landscape undergoes continuous changes and evolution. By strategically choosing and implementing the right frameworks, businesses can adapt to these shifts, enhance their security posture, and stay resilient against emerging threats.
Regulatory compliance regimes usually set out highly specific and often strict criteria to be met by organizations and under existing legislation.
Such standards can be various and nuanced – so structures designed to help satisfy compliance requirements are a welcome addition to most companies. Similar structures are often at the core of identity management, data handling, and privacy issues.
Such standards can be various and nuanced – so structures designed to help satisfy compliance requirements are a welcome addition to most companies. Similar structures are often at the core of identity management, data handling, and privacy issues.

Quickly query billions of records with Lucene or Regex, filtering by date, source, file type, actor, or keyword.
Create teams, roles, and project-based access to align the platform with your internal workflows.
Users can design and deploy their own bots directly from the interface—no coding required.
HawkINT identifies and helps remove impersonations on social networks and digital platforms.
Advanced scanning powered by AI detects phishing websites, malware hosts, and fraudulent landing pages—alerting your team immediately.
Set up recurring searches and automated monitoring for vulnerabilities, VIP mentions, leaks, and more.
Track ransomware groups, leak sites, chatter, attack disclosures, and activity trends.
Monitor exposure of company executives and sensitive individuals across the surface, deep, and dark web.
HawkINT uses cutting-edge AI to transform raw data into actionable intelligence.
AI Capabilities Include:

Prevent fraud, monitor card leaks, intercept phishing campaigns, and track threat actor groups targeting banks.
Protect patient data, comply with HIPAA, and detect unauthorized access or data marketplace activity.
Monitor hacktivist groups, geopolitical threats, and critical infrastructure risks.
Track nation-state actors, ransomware groups, and critical infrastructure threats.
When HawkINT detects threats—like phishing pages, leaked credentials, fraud schemes, hacktivist planning, or illegal data marketplaces—the system creates “wires” with solid evidence, context, and recommendations.
sales@cybrhawk.com
Whether you’re ready to speak with someone about pricing, want to dive deeper on a specific topic, or have a problem that you’re not sure we can address, we’ll connect you with someone who can help.
2026 @ All rights reserved by CybrHawk Inc.
At TechXen IT Solutions, we’re dedicated to delivering innovative technology solutions tailored to meet the unique needs of businesses like yours.
Copyright @2025 TechXen.All Rights Reserved